Sommario
- Cos'è l'Internet delle cose industriale (IIoT)?
- In che modo l'IIoT è diverso dall'IoT?
- Qual è la differenza tra IIoT e tecnologia operativa (OT)?
- IIoT e sistemi cyber-fisici
- Standard IIoT e automazione
- IIoT e ambienti pericolosi
- Distribuzione dell'IIoT in ambienti Secure Access Service Edge (SASE)
- Difendere l'IIoT dagli attacchi informatici
- Scopri di più sull'IIoT
Cos'è l'Internet delle cose industriale (IIoT)?
L'Industrial Internet of Things (IIoT) si riferisce all'integrazione di macchinari e attrezzature industriali con sensori e software connessi in rete per raccogliere e scambiare dati. I sistemi IIoT sfruttano i dati in tempo reale e le analisi avanzate per ottimizzare le operazioni, prevedere le esigenze di manutenzione e migliorare le prestazioni industriali complessive.
L'Internet delle cose industriale (IIoT) si riferisce alla rete interconnessa di dispositivi fisici, sensori e software in ambienti industriali. I dispositivi e le applicazioni IIoT variano ampiamente e la maggior parte è progettata specificamente per applicazioni specifiche. I dispositivi IIoT supportano la raccolta e lo scambio di dati tra macchine, sistemi e persone. Questo rende possibile automatizzare i processi digitali, tracciare le risorse in tempo reale, gestire il consumo energetico e prevedere i guasti delle attrezzature in un'officina. Questi si sono tradotti in benefici aziendali come condizioni di sicurezza migliorate, catene di approvvigionamento ottimizzate e gestione energetica efficiente.
L'IIoT, noto anche come internet industriale, è emerso come un sottoinsieme dell'Internet delle cose (IoT) nei primi anni 2010. Aziende come General Electric Company (GE) e Philips Professional Lighting Solutions stavano concettualizzando e finanziando lo sviluppo di dispositivi simili all'IoT specificamente per ambienti industriali. Entro il 2014, la consapevolezza stava crescendo in diversi settori economici e i leader aziendali stavano imparando come l'IIoT potesse migliorare l'efficienza, la produttività e le operazioni aziendali. Quando il concetto di Quarta Rivoluzione Industriale (4IR) è stato reso popolare nel 2016, è rapidamente diventato intrecciato con il potenziale e la promessa dell'IIoT. La trasformazione digitale, la produzione intelligente e i sistemi ciber-fisici sono possibili grazie alle tecnologie e ai concetti dell'IIoT.
Poiché il mondo dell'IoT include dispositivi e applicazioni di livello consumer, è stata necessaria una nuova classificazione per descrivere i dispositivi che dovevano essere integrati in un flusso di lavoro industriale.
In che modo l'IIoT è diverso dall'IoT?
|
Aspetto
|
IIOT
|
IoT
|
|---|---|---|
|
Applicazione
|
Ambienti industriali
|
Ambienti per i consumatori e commerciali
|
|
Focus Primario
|
Migliorare i processi industriali e l'efficienza
|
Migliorare la comodità e la connettività della vita quotidiana
|
|
Esempi di Casi d'Uso
|
automazione della produzione, ottimizzazione della catena di approvvigionamento, manutenzione predittiva
|
Case intelligenti, dispositivi indossabili, città intelligenti, fitness personale
|
|
Tipi di dispositivi
|
Sensori industriali, controller logici programmabili (PLC) e sistemi di acquisizione dati e controllo supervisivo (SCADA)
|
Termostati intelligenti, altoparlanti intelligenti, tracker fitness
|
|
Affidabilità
|
Richiede alta affidabilità e operatività
|
Affidabilità moderata richiesta
|
|
Requisiti di sicurezza
|
Stringenti standard di sicurezza e conformità
|
Protocolli di sicurezza standard
|
|
Protocolli di comunicazione
|
Protocolli specifici per l'industria (ad esempio, Modbus, OPC-UA)
|
Protocolli internet standard (ad es., Wi-Fi, Bluetooth)
|
|
Applicazione
|
Dispositivo e funzione IIoT
|
Dispositivo IoT e funzione
|
|---|---|---|
|
Monitoraggio ambientale
|
Sensori intelligenti: Raccogliere dati su temperatura, umidità e pressione in ambienti industriali
|
Sensori ambientali: Monitora la qualità dell'aria, la temperatura e l'umidità nelle case
|
|
Automazione dei processi
|
PLC: Automatizzare i processi industriali e controllare i macchinari
|
Hub smart per la casa: Automatizza i dispositivi domestici e controlla gli elettrodomestici intelligenti
|
|
Monitoraggio remoto
|
Sistemi SCADA: Monitorare e controllare da remoto i processi industriali
|
Telecamere di sicurezza intelligenti: Monitoraggio remoto della sicurezza domestica
|
|
Gestione dell'energia
|
Contatori intelligenti: Monitorare e ottimizzare il consumo energetico nelle strutture industriali
|
Termostati intelligenti: gestire i sistemi di riscaldamento e raffreddamento domestico per risparmiare energia
|
|
Sicurezza e conformità
|
Sistemi strumentati di sicurezza (SIS): Garantire la sicurezza nei processi industriali critici
|
Rilevatori di fumo: Rilevano il fumo e avvertono gli utenti di potenziali incendi
|
|
Elaborazione dati
|
Dispositivi di edge computing: Processano i dati localmente al margine della rete in ambienti industriali
|
Smart speaker: Elaborano comandi vocali e controllano dispositivi smart home
|
Qual è la differenza tra IIoT e tecnologia operativa (OT)?
I sistemi di tecnologia operativa (OT) monitorano e controllano i processi fisici e i dispositivi negli ambienti industriali. Il concetto è emerso negli anni '60 quando i primi sistemi SCADA e PLC sono stati utilizzati nella produzione. L'OT comprende diverse tecnologie che sono classificate per applicazione:
- Controllori logici programmabili (PLC): Automazione e controllo dei processi industriali
- Sistema di controllo e acquisizione dati (SCADA): Monitoraggio e controllo remoto
- Sistemi di controllo distribuito (DCS): Controllo localizzato dei processi di produzione
- Sistemi di controllo industriale (ICS): Sistemi di controllo completi nella produzione industriale
- Sistemi di gestione degli edifici (BMS): Gestione dei servizi degli edifici
- Interfacce uomo-macchina (HMI): Interfacce per l'interazione umana con i sistemi di controllo
- Sistemi strumentati di sicurezza (SIS): Controllo dei processi critici per la sicurezza
- Sistemi di gestione dell'energia (EMS): Monitoraggio e ottimizzazione dei sistemi energetici
- Sistemi di esecuzione della produzione (MES): Gestione delle operazioni sul pavimento della fabbrica (Questi possono anche essere chiamati sistemi di gestione delle operazioni di produzione (MOM).)
- Sistemi di controllo di processo: Controllo automatico dei processi industriali
L'IIoT estende le capacità dell'OT abilitando la raccolta, l'analisi e le intuizioni dei dati in tempo reale attraverso un'intera operazione industriale. La tecnologia operativa si concentra sul controllo di processi specifici e l'IIoT consente l'approccio interconnesso alla gestione e ottimizzazione industriale.
IIoT e sistemi cyber-fisici
|
Aspetto
|
Sistemi cibernetici-fisici (CPS)
|
Internet industriale delle cose (IIoT)
|
|---|---|---|
|
Definizione
|
Integrazione di processi computazionali, di rete e fisici
|
Sensori, strumenti e dispositivi interconnessi nelle applicazioni industriali
|
|
Componenti principali
|
Computer embedded, reti, processi fisici
|
Sensori, dispositivi, reti di comunicazione, analisi dei dati
|
|
Focus Primario
|
Monitoraggio e controllo in tempo reale dei processi fisici
|
Connettività, raccolta dati, automazione e ottimizzazione dei processi industriali
|
|
Applicazioni
|
Reti intelligenti, veicoli autonomi, monitoraggio medico, controllo industriale, robotica
|
Produzione, gestione dell'energia, automazione industriale, manutenzione predittiva
|
|
Obiettivo
|
Migliorare l'efficienza, l'affidabilità e la sicurezza dei sistemi fisici
|
Migliora la produttività, l'efficienza e la sicurezza negli ambienti industriali
|
Standard IIoT e automazione
L'IIoT richiede un modello standard per garantire l'interoperabilità tra dispositivi e sistemi. È inoltre necessario mappare l'IIoT e altre tecnologie industriali sui processi aziendali in modo che le aziende possano adottare e ottimizzare l'uso di questi sistemi. L'ISA-95 è lo standard internazionale per l'integrazione dei sistemi aziendali e di controllo. In parole povere, l'ISA-95 aiuta le aziende a capire come integrare l'IIoT e l'OT per supportare diverse funzioni aziendali.
L'IIoT ha un ruolo in ciascuno dei cinque livelli dello standard ISA-95:
- Livello 0: I processi fisici non sono dispositivi IIoT, ma i dispositivi IIoT li monitorano e li controllano.
- Livello 1: Sensori e attuatori sono dispositivi core IIoT.
- Livello 2: I sistemi di controllo possono essere abilitati all'IIoT.
- Livello 3: I sistemi MES possono sfruttare i dati IIoT e possono far parte dell'ecosistema IIoT.
- Livello 4: I sistemi di pianificazione delle risorse aziendali (ERP) utilizzano i dati dei dispositivi IIoT per una gestione aziendale più ampia.
La piramide di automazione ISA-95 mostra le relazioni tra i livelli, i sistemi OT e i processi aziendali standard:
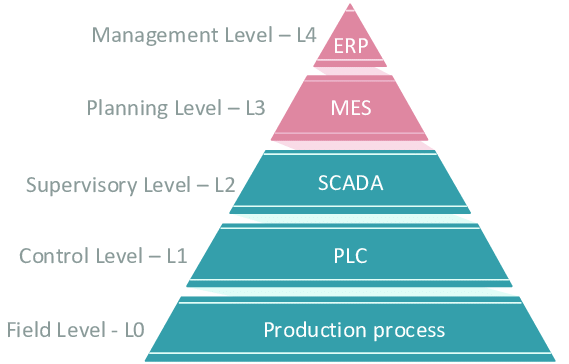
La piramide dell'automazione ISA-95.
Lo scenario seguente è un esempio di come questo modello funziona in un ambiente di smart manufacturing:
- La salute di una macchina di fabbrica di Livello 0 è monitorata da un sensore di Livello 1 abilitato per IIoT.
- I sensori inviano dati a un sistema SCADA di Livello 2, che elaborerà e analizzerà i dati in tempo reale.
- Il sistema SCADA comunica con il MES di Livello 3 per regolare i programmi di produzione in risposta ai cambiamenti nella salute/performance delle macchine.
- Il MES comunica questi dati al livello 4 ERP per facilitare la gestione di quelle aree interessate da questi aggiustamenti produttivi.
IIoT e ambienti pericolosi
Poiché i dispositivi IIoT sono fondamentali per il settore manifatturiero e le infrastrutture critiche, vengono spesso utilizzati in ambienti fisici difficili. Condizioni meteorologiche avverse, temperature estreme e polvere o altre particelle possono interferire con i sensori e altri componenti IIoT. Questi dispositivi devono essere resilienti e rimanere in produzione perché si applicano a infrastrutture critiche o altre funzioni ad alta priorità. I sensori di terremoti e vulcani possono aiutare i professionisti a prevedere i disastri naturali e potenzialmente salvare vite umane, ma solo se quei sensori funzionano correttamente e non sono compromessi dalla corrosione, dalle particelle o dalle temperature estreme.
Ci sono molti di questi dispositivi in luoghi come il Parco Nazionale di Yellowstone, dove i funzionari monitorano vari fenomeni naturali per aiutare a prevedere l'attività vulcanica o sismica. Le stazioni di monitoraggio continuo consentono alle squadre di raccogliere dati sui livelli di emissione, anche quando le abbondanti nevicate limitano il viaggio attraverso il parco. Molte località protette come il Parco Nazionale di Yellowstone hanno anche aree sensibili che i funzionari del parco e i membri del pubblico dovrebbero evitare. I sistemi di monitoraggio remoto resilienti possono fornire ai funzionari ciò di cui hanno bisogno e ridurre al minimo l'interazione umana con queste aree fragili.

Stazioni di monitoraggio delle emissioni nel Parco Nazionale di Yellowstone
I sistemi acustici subacquei monitorano la velocità e la direzione dell'acqua per aiutare a identificare e prevedere l'attività delle onde. I cavi in fibra ottica dispiegati attraverso vulcani attivi aiutano le autorità a rilevare segnali di sforzo vulcanico e a individuare le origini delle esplosioni. Questi sono esempi di attività che salvano vite rese possibili da sistemi robusti in grado di resistere a un ambiente ostile senza compromettere la sensibilità del dispositivo.
Esistono molti usi aziendali e infrastrutturali per l'implementazione di IIoT in ambienti difficili. La produzione e il trasporto di alimenti e medicinali possono richiedere un monitoraggio continuo delle deviazioni di temperatura, umidità o qualità dell'aria. Stazioni meteorologiche, sottostazioni elettriche, tubi dell'acqua municipali e persino binari ferroviari sono dotati di sensori IIoT che necessitano di protezione costante dai pericoli ambientali.
Per questo motivo, la pianificazione dell'implementazione IIoT dovrebbe sempre considerare l'ambiente di implementazione. Custodie impermeabili e robuste possono proteggere il dispositivo IIoT da polvere, acqua, corrosione chimica e altri pericoli. I requisiti per questi dispositivi di solito includono livelli di protezione dall'ingresso (IP) migliorati, resistenza agli urti e alle vibrazioni, e un intervallo esteso di temperatura operativa e umidità operativa. Considera anche la dimensione del dispositivo, soprattutto se verrà installato in un armadio o in un altro spazio ristretto.
Distribuzione dell'IIoT in ambienti Secure Access Service Edge (SASE)
|
elemento SASE
|
Ruolo nel SASE
|
Supporto per IIoT
|
|---|---|---|
|
Distribuzione zero-touch
|
Abilita il provisioning e la configurazione automatizzati delle risorse di rete e di sicurezza senza intervento manuale
|
Facilita l'onboarding rapido e scalabile dei dispositivi IIoT, riducendo il tempo di distribuzione e i costi operativi. Ciò rende anche la distribuzione meno soggetta a errori umani e più facile da scalare verso l'alto o verso il basso secondo necessità.
|
|
Zero Trust security
|
Garantisce una verifica rigorosa dell'identità e il monitoraggio continuo per tutti i dispositivi e gli utenti, indipendentemente dalla posizione
|
Protegge le reti IIoT verificando ogni dispositivo e utente prima di concedere l'accesso, riducendo il rischio di violazioni
|
|
Microsegmentazione
|
Divide la rete in segmenti più piccoli e isolati per limitare il movimento laterale delle minacce
|
Isola i dispositivi e i sistemi IIoT per contenere potenziali violazioni e minimizzare l'impatto degli attacchi
|
|
Gestione centralizzata
|
Fornisce una piattaforma unificata per la gestione delle politiche di rete e di sicurezza in tutta l'azienda
|
Semplifica la gestione delle implementazioni IIoT offrendo un'unica interfaccia per controllare le misure di sicurezza e monitorare le prestazioni dei dispositivi
|
|
Applicazione coerente delle politiche di sicurezza
|
Garantisce che i criteri di sicurezza siano applicati uniformemente su tutti i segmenti di rete e punti di accesso
|
Mantiene standard di sicurezza uniformi per tutti i dispositivi IIoT, indipendentemente dalla loro posizione, garantendo una protezione completa
|
|
Visibilità a livello aziendale
|
Fornisce una visibilità olistica dell'attività di rete e degli eventi di sicurezza in tutta l'organizzazione
|
Migliora il monitoraggio dei dispositivi e delle reti IIoT, consentendo il rilevamento e la risposta tempestiva alle potenziali minacce
|
Difendere l'IIoT dagli attacchi informatici
Per proteggere la tua internet industriale dagli attacchi informatici, è necessario includere diverse best practice e strategie nella pianificazione della sicurezza informatica della tua azienda. Di seguito sono riportati alcuni aspetti comuni da considerare quando si difendono gli IIoT e altri dispositivi dalle minacce avanzate:
- Sicurezza Zero Trust: Nessun dispositivo, utente o applicazione è considerato attendibile di default. È necessaria una verifica continua.
- Segmentazione della rete: Dividere la rete in segmenti più piccoli per limitare la diffusione degli attacchi.
- Aggiornamenti e patch regolari: Mantieni tutti i dispositivi, software e applicazioni aggiornati con le ultime patch di sicurezza.
- Crittografia: Crittografa i dati a riposo e in transito per proteggere le informazioni sensibili dall'accesso non autorizzato.
- Sicurezza degli endpoint: Assicurarsi che tutti gli endpoint (dispositivi) abbiano misure di sicurezza come antivirus, anti-malware e sistemi di rilevamento delle intrusioni installati.
- Controlli di accesso / privilegio minimo: Limita l'accesso ai dispositivi e sistemi IIoT solo a chi ne ha bisogno.
- Monitoraggio e registrazione: Monitorare continuamente il traffico di rete e mantenere i registri per rilevare e rispondere tempestivamente ad attività sospette.
- Formazione dei dipendenti: Educare i dipendenti sui rischi associati ai dispositivi IIoT.
Le aziende con dispositivi legacy che sono oltre la fine del ciclo di vita potrebbero desiderare di integrare l'elenco sopra con il seguente:
- Patch virtuale: Distribuire sistemi di prevenzione delle intrusioni (IPS) o firewall per applicazioni web (WAF) che possono rilevare e bloccare tentativi di exploit senza richiedere modifiche.
- Controllo degli accessi alla rete (NAC): In assenza di sicurezza Zero Trust, configura il NAC per autenticare dispositivi e utenti prima di concedere l'accesso alla rete e monitora continuamente i dispositivi non autorizzati.
- Difesa del perimetro: Implementa soluzioni di sicurezza di rete con protezione avanzata dalle minacce, rilevamento/prevenzione delle intrusioni e altre funzionalità avanzate.
- Audit e valutazioni: Pianifica audit periodici dei sistemi IIoT e dell'infrastruttura di rete per identificare e affrontare le lacune di sicurezza o questioni di conformità.
Una piattaforma SASE unificata fornisce criteri e controlli di sicurezza coerenti su tutti i dispositivi, utenti e luoghi, indipendentemente da dove siano distribuiti i dispositivi IIoT. SASE applica la sicurezza al bordo della rete, avvicinando l'applicazione dei criteri al dispositivo IIoT. La natura basata su cloud di SASE consente una gestione della sicurezza più scalabile e flessibile, aggiornamenti più semplici e integrazione dell'intelligence sulle minacce in tempo reale.
Scopri di più sull'IIoT
Termini correlati
- Accesso remoto
- SASE (Secure Access Service Edge)
- Firewall-as-a-Service? (FWaaS)
- Sicurezza IoT
- Perimetro di rete
- Accesso Zero Trust (ZTA)
Ulteriori letture
- Definire i sistemi ciber-fisici e altri 'oggetti' connessi
- Produzione cloud e il suo ruolo nella 4ª rivoluzione industriale
- L'Industria 4.0 sfuma i confini tra IT e OT
- Gli attacchi informatici minacciano le operazioni aziendali e le infrastrutture critiche
- IIoT: Un fattore chiave e vettore di minacce per l'Industria 4.0
- L'IoT industriale può diventare un mercato fiorente per i provider di servizi gestiti (MSP)
- Come l'IoT si integra nel SASE
- Proteggere gli oggetti intelligenti sta diventando più difficile e più importante
- Sicurezza della tecnologia operativa (OT) nel 2024
In che modo Barracuda può essere di aiuto
Le soluzioni Barracuda aiutano i produttori e le aziende industriali a proteggere i loro asset e sistemi di controllo dalle minacce informatiche avanzate. Barracuda CloudGen Firewall Rugged combina la sicurezza completa di nuova generazione per implementazioni in ambienti difficili con il set di funzionalità specifico per i requisiti della tecnologia operativa. Barracuda Secure Connector offre protezione avanzata e connettività conveniente per qualsiasi dimensione di implementazione IIoT.
Barracuda fornisce una piattaforma completa di sicurezza informatica che include funzionalità avanzate di sicurezza e connettività per dispositivi connessi a Internet e tecnologia operativa. Barracuda offre soluzioni complete, ricche di funzionalità e dal miglior rapporto qualità-prezzo che proteggono da un'ampia gamma di vettori di minaccia e sono supportate da un servizio clienti completo e premiato. Poiché si lavora con un unico fornitore, si beneficia di una complessità ridotta, un'efficacia aumentata e un costo totale di proprietà inferiore. Centinaia di migliaia di clienti in tutto il mondo si affidano a Barracuda per proteggere le loro e-mail, reti, applicazioni e dati.