Sommario
- Cos'è l'accesso sicuro a Internet (SIA)?
- Perché SIA è importante?
- Domini principali di Secure Internet Access (SIA)
- Funzioni principali di SIA
- Componenti principali di SIA
- Come funziona SIA?
- SIA e Secure Access Service Edge (SASE)
- SIA e conformità normativa
- Accesso Internet sicuro e lavoro da remoto
- Scopri di più su Secure Internet Access (SIA)
Cos'è l'accesso sicuro a Internet (SIA)?
L'accesso sicuro a Internet (SIA) si riferisce alle misure e alle tecnologie che proteggono la connessione tra l'endpoint e Internet. SIA garantisce la privacy e l'integrità dei dati e offre un'esperienza di navigazione sicura. Comprende una gamma di pratiche e tecnologie per proteggere reti, dispositivi e dati.
Il concetto di SIA si è sviluppato insieme allo sviluppo di internet, ma non era al centro dell'attenzione degli utenti fino all'emergere di protocolli di sicurezza come il Secure Sockets Layer (SSL) e il Transport Layer Security (TLS) alla fine degli anni '90. Gli hacker dannosi lanciavano continuamente nuovi virus, Trojan e altri attacchi. Le tecnologie di sicurezza continuarono a migliorare e ad espandersi, portando a prodotti come software anti-virus/spyware, filtri web, firewall e browser web con crittografia (HTTPS) e altri strumenti di sicurezza. L'eventuale emergere della Zero Trust Security ha cambiato il paradigma intorno alla SIA, e la sicurezza internet è diventata un dominio più ampio di protezione dalle minacce.
La SIA moderna include molti componenti e funzioni, ma questi componenti e funzioni sono più accessibili e più forti che mai. Quasi tutto il traffico aziendale degli utenti finali è basato sul web e utilizza il protocollo HTTPS per inviare dati attraverso Internet. Le pratiche e le tecnologie SIA sono un requisito per le aziende e gli individui che si affidano ad applicazioni web e attività aziendali basate su Internet. Ad esempio:
- Ospedali, cliniche e altri fornitori di servizi sanitari utilizzano SIA per proteggere le informazioni dei pazienti e conformarsi al Health Insurance Portability and Accountability Act (HIPPA) e ad altri regolamenti sulla protezione dei dati.
- Entità governative utilizzano SIA per proteggere i dati sensibili e mantenere la sicurezza nazionale proteggendosi dall' spionaggio informatico e da altre minacce. Il governo federale degli Stati Uniti ha diverse iniziative SIA, tra cui il programma Trusted Internet Connections (TIC) e il servizio di accesso sicuro Login.gov.
- Scuole, università e altre istituzioni educative utilizzano SIA per proteggere le informazioni personali, le transazioni finanziarie, i dati di ricerca e molti altri tipi di informazioni. SIA è anche necessaria per mantenere un ambiente di apprendimento sicuro, che è un requisito normativo per molte scuole.
- Gli utenti internet individuali si affidano a SIA per proteggere i loro dati personali e la loro privacy mentre navigano sul web, fanno shopping online o utilizzano servizi bancari online. La maggior parte di questi servizi richiederà un livello di sicurezza di base, che può includere browser web aggiornati, un livello minimo di crittografia e una sfida CAPTCHA progettata per fermare i bot e garantire che solo un utente umano possa accedere a un account.
Perché SIA è importante?
L'accesso sicuro a Internet è necessario per proteggere gli endpoint di rete e i dati trasmessi tra di essi. Questa sicurezza è stata fondamentale per la crescita di Internet, del software come servizio e di altre applicazioni web. L'accesso sicuro a Internet è stato vitale per la trasformazione digitale e la continuità operativa delle aziende e dei governi di tutto il mondo. La Quarta Rivoluzione Industriale e lo sviluppo di sistemi cibernetico-fisici dipendono dalla capacità di proteggere le aziende e i loro dati dalle minacce online.
Le moderne soluzioni SIA estendono la sicurezza della rete aziendale oltre la sede centrale e le filiali. Questo consente alle aziende di utilizzare una forza lavoro remota o ibrida senza mettere a rischio la rete. Alcuni scenari d'uso richiedono SIA anche quando il traffico non raggiunge Internet. I fornitori di assistenza sanitaria a volte utilizzano software di cartelle cliniche elettroniche (EHR) basati sul web che sono ospitati in sede. Questo scenario richiede alcuni componenti SIA per proteggere questo traffico HTTPS, anche se il sistema è ospitato e accessibile localmente.
Domini principali di Secure Internet Access (SIA)
La maggior parte di SIA opera entro tre domini di protezione:
Privacy dei dati: Questo comporta il controllo dell'accesso ai dati sensibili e la determinazione delle parti che possono accedere e condividere dati sensibili. I controlli sulla privacy dei dati includono l'autenticazione e l'autorizzazione, tecnologie di crittografia e politiche di privacy stabilite dall'azienda e applicate attraverso configurazioni di sicurezza. Quest'area della sicurezza garantisce che le informazioni personali o riservate non siano compromesse e utilizzate in modo improprio.
Integrità dei dati: Nel contesto di SIA, l'integrità dei dati consiste nel garantire che i dati rimangano accurati, completi e coerenti durante la trasmissione. Questo dominio si occupa principalmente di funzioni come il controllo degli errori, la crittografia e altre funzioni che impediscono agli attaccanti di manomettere i dati. Dati accurati e affidabili sono necessari per la conformità normativa e l'intelligence aziendale.
Prevenzione delle minacce: Gli attacchi informatici sono una preoccupazione importante per ogni azienda e individuo che conduce affari su Internet. L'accesso sicuro a Internet difende da malware, attacchi di phishing, violazioni dei dati, intrusioni, esfiltrazione dei dati e altro ancora. Le aziende spesso configurano misure di sicurezza per il cloud o il data center per integrare l'SIA dell'endpoint. Questo include soluzioni come firewall e protezione perimetrale, sistemi di rilevamento/prevenzione delle intrusioni e filtraggio dei contenuti. Le robuste capacità dell'SIA proteggono gli endpoint e la rete aziendale da ransomware, phishing e altre minacce.
Funzioni principali di SIA
La SIA moderna incorpora una manciata di principi e funzionalità che rientrano in uno o più dei tre domini sopra menzionati. Questi includono:
- Ispezione del traffico: SIA esamina tutto il traffico internet in entrata e in uscita. Analizza URL, file e contenuti per identificare potenziali minacce. Questo si allinea strettamente con il sistema di rilevamento malware.
- Rilevamento e prevenzione del malware: SIA blocca l'accesso ai siti dannosi o compromessi, previene i download di malware e rileva i tentativi di intrusione. I download vengono ispezionati in un ambiente sandbox e sanitizzati per la consegna o bloccati dal endpoint.
- Filtraggio dei contenuti: Questo comporta l'applicazione di politiche di sicurezza della navigazione web. Questo filtraggio si basa principalmente su categorie web come social media, giochi e contenuti per adulti. La maggior parte delle soluzioni di filtraggio dei contenuti consente la personalizzazione in base alle esigenze del dipartimento. Ad esempio, il team responsabile dei social media avrebbe bisogno di accesso ai siti web nella categoria social media.
- Prevenzione delle perdite di dati (DLP): SIA aiuta a prevenire la perdita di dati sensibili monitorando e controllando i trasferimenti di dati. Queste funzionalità bloccano la condivisione o l'archiviazione di informazioni sensibili su social media non autorizzati, applicazioni SaaS e servizi di condivisione file.
- Crittografia e decrittografia: L'HTTPS e altri traffici crittografati possono nascondere contenuti dannosi e minacce. Questa funzione SIA decrittograferà il traffico per analizzare i contenuti alla ricerca di segni di malware, phishing e altri attacchi. Ciò garantisce una comunicazione sicura e fornisce visibilità sul comportamento degli utenti e sui rischi potenziali.
- Autenticazione utente: La gestione degli accessi e delle identità (IAM) esegue l'autenticazione e l'autorizzazione e determina l'accesso appropriato in base all'identità.
- Integrazione nel cloud: Firewall-as-a-service, secure web gateways e molte altre soluzioni SIA sono nativi del cloud. I componenti endpoint, come gli strumenti di rilevamento e risposta degli endpoint (EDR), si integrano con i servizi cloud, rendendo la sicurezza sul dispositivo più intelligente e facile da gestire. In generale, il cloud offre alle aziende sicurezza di livello enterprise sul dispositivo, oltre alla flessibilità di scalare il deployment verso l'alto o verso il basso secondo necessità.
- Rilevamento di phishing: L'intelligenza artificiale, l'analisi euristica e molte altre tecnologie lavorano insieme per rilevare, prevenire e mitigare gli attacchi informatici. Questo include gli attacchi di phishing, che SIA può prevenire ispezionando moduli web, campi password e altri potenziali indicatori di phishing. SIA si difende anche dagli attacchi di phishing con i suoi molti altri meccanismi di sicurezza, come il filtraggio degli URL, l'ispezione dei contenuti e la prevenzione del malware.
- Prevenzione e rilevamento delle intrusioni: Questi sistemi monitorano i flussi di traffico di rete per attività sospette o segni di attacchi. Il rilevamento può essere basato su analisi del comportamento o firme che confrontano l'attività con un database di minacce conosciute. I sistemi di prevenzione spesso rispondono al rilevamento eliminando pacchetti dannosi, bloccando indirizzi IP e avvisando i team di sicurezza della potenziale minaccia.
- Isolamento del browser remoto (RBI): Questa funzione isola l'attività del browser non attendibile dai dispositivi utente e dalle reti aziendali. Normalmente, ciò comporta l'esecuzione di pagine web e codice associato su un server remoto piuttosto che sul dispositivo dell'utente. RBI eliminerà anche eventuali cookie o download dannosi al termine della sessione.
- Gestione unificata e analisi: Le soluzioni SIA di livello enterprise offrono una piattaforma di gestione unificata che fornisce una visione olistica e un controllo granulare sulle capacità di sicurezza. Questo include l'analisi per identificare incidenti di sicurezza, comportamenti insoliti e violazioni delle policy.
SIA integra molteplici tecnologie di sicurezza per proteggere endpoint, reti e dati. I fornitori di sicurezza possono variare nelle loro implementazioni, ma quasi tutte le soluzioni SIA aziendali contengono queste funzioni fondamentali.
Componenti principali di SIA
Le funzioni sopra menzionate sono solitamente fornite dai seguenti componenti:
- Firewall o Firewall-as-a-Service (FWaaS): Questi creano una barriera di sicurezza tra una rete fidata e una rete non fidata. Ciò previene l'accesso non autorizzato e blocca il traffico dannoso. I sistemi di rilevamento delle intrusioni e di protezione dalle intrusioni sono spesso inclusi qui, anche se possono essere una soluzione separata o distribuiti su più componenti.
- Sistema di rilevamento delle intrusioni (IDS): Un IDS monitora il traffico di rete per rilevare attività sospette e emette avvisi quando tale attività viene rilevata. Questo sistema aiuta nella rilevazione precoce di potenziali minacce, consentendo un intervento tempestivo per prevenire violazioni della sicurezza.
- Sistema di prevenzione delle intrusioni (IPS): Un IPS non solo rileva, ma previene anche le minacce identificate dal causare danni. Bloccando il traffico dannoso in tempo reale, un IPS offre un approccio proattivo alla sicurezza della rete, complementare all'IDS.
- Software antivirus (AV): Protezione degli endpoint che rileva, previene e rimuove malware, virus, worm e altri software dannosi. La maggior parte delle soluzioni AV moderne analizza i file e monitora le attività del sistema in tempo reale, rispondendo immediatamente alle minacce.
- Secure web gateway (SWG): Il SWG blocca l'accesso a siti web dannosi e previene l'esposizione a contenuti nocivi. L'intelligence sulle minacce in tempo reale consente al SWG di difendersi dagli attacchi zero-day e altre minacce emergenti.
- Protezione avanzata dalle minacce (ATP): Le soluzioni ATP rilevano, prevengono e rispondono alle minacce informatiche sofisticate, inclusi gli exploit zero-day. Questo componente difende il sistema dalle minacce persistenti avanzate (APT) e da altri attacchi sofisticati.
- Zero Trust Network Access (ZTNA): ZTNA verifica ogni richiesta di accesso prima di concedere l'autorizzazione. Questo impone una rigorosa verifica dell'identità e del dispositivo per tutti gli utenti e riduce al minimo il rischio di accessi non autorizzati.
Ogni componente di SIA contribuisce a un quadro di sicurezza solido e completo ed è una parte essenziale delle strategie di sicurezza informatica moderne. Questo è particolarmente vero in ambienti con forza lavoro remota e ibrida.
Come funziona SIA?
I componenti sopra elencati collaborano per fornire un flusso di lavoro sicuro e completo. Ecco un riepilogo di ciò che accade dietro le quinte di SIA:
- Autenticazione e autorizzazione dell'utente: Prima di accedere alla rete, gli utenti devono autenticarsi utilizzando metodi sicuri, come l'autenticazione multifattoriale (MFA). Questo garantisce che solo gli utenti autorizzati possano accedere alle risorse di rete.
- Monitoraggio e filtraggio del traffico: I firewall, SWG e NGFW monitorano il traffico in entrata e in uscita, bloccando qualsiasi traffico che non rispetti le politiche di sicurezza. Questo filtraggio aiuta a prevenire l'ingresso di traffico dannoso nella rete.
- Rilevamento e prevenzione delle minacce: IDS e IPS lavorano in tandem per rilevare e bloccare potenziali minacce. IDS allerta gli amministratori su attività sospette, mentre IPS previene attivamente che queste minacce causino danni.
- Crittografia dei dati e trasmissione sicura: Le soluzioni DLP garantiscono che i dati trasmessi sulla rete siano crittografati e protetti da intercettazioni. DLP monitora anche i trasferimenti di dati per prevenire la perdita di dati non autorizzata.
- Monitoraggio continuo e risposta: ATP e ZTNA forniscono monitoraggio e analisi continui delle attività di rete. ATP rileva e mitiga le minacce avanzate, mentre ZTNA applica controlli di accesso rigorosi, garantendo che solo utenti e dispositivi verificati possano accedere alla rete.
- Reporting e indagine: Il sistema registra il traffico DNS, HTTP e HTTPS. I team SIA e di sicurezza possono monitorare le attività degli utenti e indagare su tutti i rischi potenziali e le minacce rilevate.
SIA e Secure Access Service Edge (SASE)
L'accesso sicuro a Internet è un componente fondamentale delle implementazioni Security Service Edge (SSE) e SASE. Opera nell'ultimo miglio di questi modelli di sicurezza.
SASE è un framework di architettura di rete che combina funzioni di sicurezza di rete (come gateway web sicuri, firewall e accesso alla rete Zero Trust) con funzionalità di rete WAN. Questa integrazione è fornita tramite un singolo modello di servizio cloud.
SSE è un sottoinsieme di SASE focalizzato specificamente sui servizi di sicurezza. Le aziende potrebbero implementare un modello di sicurezza SSE come primo passo verso una completa implementazione di SASE. Questo è comune quando l'azienda ha già un'infrastruttura di rete robusta o un budget limitato che restringe l'ambito dei progetti IT.
Ecco uno sguardo semplificato alla relazione tra SASE e SSE:
Mentre SASE integra sia i servizi di rete che quelli di sicurezza, SSE si concentra esclusivamente sugli aspetti di sicurezza.
All'interno del modello SSE, SIA garantisce un accesso sicuro ai servizi Internet. All'interno di un modello SASE completo, SIA offre funzionalità di rete aggiuntive. È tecnicamente possibile implementare SSE e SASE senza un accesso sicuro a Internet, ma questo creerebbe un divario critico nella sicurezza.
L'accesso sicuro a Internet è necessario per proteggere l'ultimo miglio, che si riferisce al segmento finale della connessione di rete tra l'utente finale e i servizi cloud o il data center. Proteggere l'ultimo miglio è impegnativo perché coinvolge una varietà di tipi di connessione potenzialmente insicuri, come il Wi-Fi domestico e le connessioni Internet pubbliche.
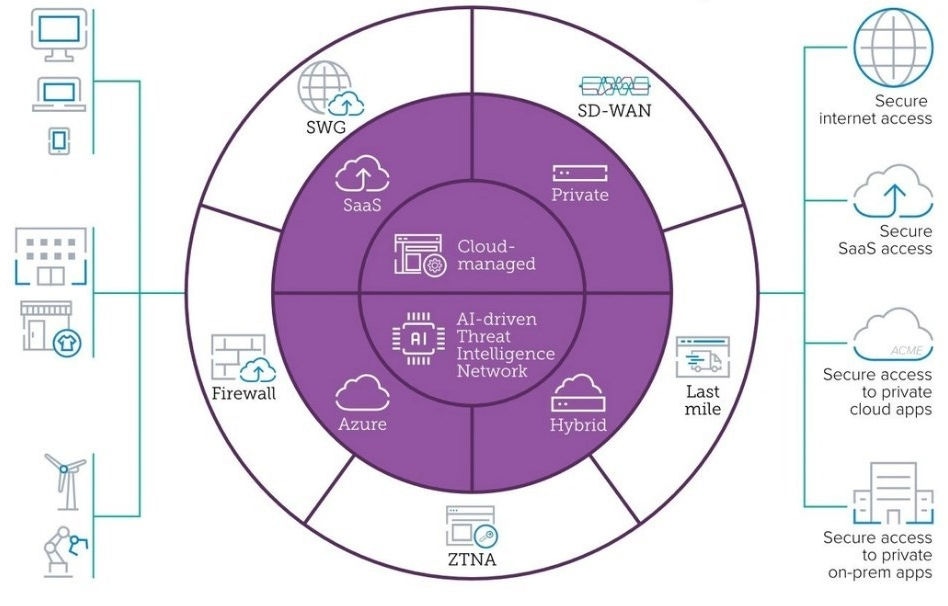
Illustrazione semplificata dell'implementazione SASE che mostra l'ultimo miglio
SIA e conformità normativa
Gli ambienti normativi variano, ma tutti possono beneficiare dell'applicazione coerente delle funzionalità e pratiche SIA:
- Le soluzioni SIA offrono capacità di registrazione e reporting dettagliate che catturano e registrano tutte le attività di rete, facilitando la dimostrazione della conformità durante gli audit.
- crittografando i dati in transito e a riposo, SIA garantisce che le informazioni sensibili siano protette secondo le linee guida normative, come GDPR, HIPAA e PCI-DSS.
- SIA applica politiche di sicurezza che sono allineate agli standard normativi, garantendo che i controlli di accesso, le misure di protezione dei dati e i meccanismi di rilevamento delle minacce soddisfino i requisiti di conformità.
- Le tracce di audit complete di SIA forniscono un registro di tutte le attività legate alla sicurezza, facilitando la verifica della conformità e le indagini sugli incidenti.
- Le soluzioni SIA ricevono aggiornamenti regolari di intelligence, sicurezza e funzionalità. Questi aggiornamenti affrontano nuove vulnerabilità e rispettano gli ultimi standard e regolamenti di sicurezza.
- I programmi di formazione e sensibilizzazione degli utenti inclusi in alcune soluzioni SIA aiutano i dipendenti a comprendere e rispettare i requisiti normativi.
Accesso Internet sicuro e lavoro da remoto
Dall'inizio dei lockdown dovuti al COVID-19, le tecnologie di accesso sicuro a Internet hanno svolto un ruolo cruciale nella sicurezza della forza lavoro remota e ibrida. Il rapido passaggio al lavoro da remoto ha messo in luce vulnerabilità nei modelli di sicurezza tradizionali, spingendo le organizzazioni ad adottare soluzioni SIA per proteggere la loro forza lavoro distribuita.
Le aziende hanno continuato a beneficiare di queste soluzioni SIA mentre si sono adattate alla forza lavoro e all'ambiente aziendale post-lockdown:
- Maggiore sicurezza: SIA ha ridotto significativamente il rischio di attacchi informatici, violazioni dei dati e accessi non autorizzati. Le soluzioni di accesso a Internet sicuro garantiscono che i lavoratori da remoto e ibridi possano operare in sicurezza.
- Produttività migliorata: I dipendenti possono lavorare da qualsiasi luogo senza compromettere la sicurezza. Questo consente loro di accedere in modo sicuro alle risorse aziendali, collaborare efficacemente e mantenere alte prestazioni.
- Efficienza dei costi: Le soluzioni di sicurezza basate su cloud possono sostituire hardware on-premises più costosi. Queste soluzioni di solito hanno una gestione centralizzata, che aiuta i team IT a ridurre il tempo dedicato alle attività amministrative. La scalabilità delle soluzioni cloud consente alle aziende di adattare il loro consumo di cloud secondo necessità, evitando così di pagare per più di quanto utilizzano.
- Esperienza utente migliorata: Tecnologie come l'isolamento del browser remoto e la sicurezza del cloud offrono un accesso fluido e sicuro alle applicazioni web e cloud senza interrompere l'esperienza dell'utente.
Scopri di più su Secure Internet Access (SIA)
Termini correlati
- Cos'è un Firewall-as-a-Service?
- Che cos'è il Software come Servizio (SaaS)?
- Cos'è il Secure Access Service Edge (SASE)? Cosa significa SASE?
- Che cos'è il filtraggio web?
- Cos'è il filtraggio degli URL?
- Cos'è l'Accesso Zero Trust (ZTA)? Cos'è l'Accesso alla Rete Zero Trust (ZTNA)?
Ulteriori letture
- Protezione degli endpoint SASE e accesso remoto sicuro
- Costruire una strategia di difesa stratificata con Firewall-as-a-Service integrato e Secure Web Gateway
- Come funziona SASE per connettere rete, sicurezza e cloud
- Come Azure e Barracuda SecureEdge proteggono la tua azienda
- Dalla crisi alla continuità: Proteggere il lavoro da remoto a lungo termine
- Pagina panoramica del prodotto: Barracuda SecureEdge
- Pagina di panoramica del prodotto: Barracuda Cybersecurity Platform
In che modo Barracuda può essere di aiuto
L'accesso sicuro a Internet (SIA) è una caratteristica chiave in Barracuda SecureEdge, una piattaforma SASE cloud-first che esegue ispezioni di sicurezza e applicazione delle policy nel cloud, presso la filiale o sul dispositivo. Barracuda SecureEdge fornisce sicurezza di livello enterprise, consentendo alle aziende di controllare l'accesso ai dati da qualsiasi dispositivo, in qualsiasi momento e luogo. SecureEdge include SIA e supporto al lavoro da remoto con funzionalità come Zero Trust Network Access (ZTNA), Firewall-as-a-Service, sicurezza web e connettività office completamente integrata con Secure SD-WAN.
Barracuda offre soluzioni all-in-one con il miglior rapporto qualità-prezzo, ricche di funzionalità, che proteggono da un'ampia gamma di vettori di minaccia e sono supportate da un servizio clienti completo e pluripremiato. Poiché si lavora con un unico fornitore, si beneficia di una complessità ridotta, un'efficacia aumentata e un costo totale di proprietà inferiore. Centinaia di migliaia di clienti in tutto il mondo si affidano a Barracuda per proteggere le loro e-mail, reti, applicazioni e dati.